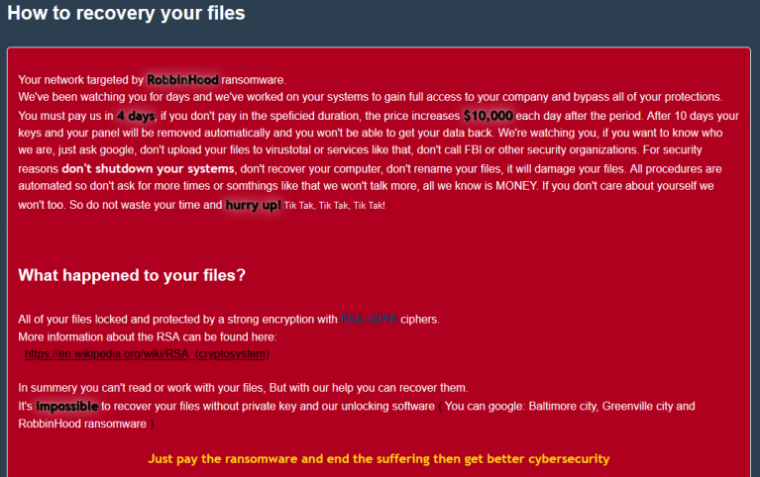
Enlarge / A note left behind by the RobbinHood malware. (credit: Sophos)
Attackers behind one of the world’s more destructive pieces of ransomware have found a new way to defeat defenses that might otherwise prevent the attack from encrypting data: installing a buggy driver first and then hacking it to burrow deeper into the targeted computer.
The ransomware in this case is RobbinHood, known for taking down the city of Baltimore networks and systems in Greenville, North Carolina. When networks aren’t protected by robust end-point defenses, RobbinHood can easily encrypt sensitive files once a vulnerability has allowed the malware to gain a toehold. For networks that are better fortified, the ransomware has a harder time.
Now, RobbinHood has found a way to defeat those defenses. In two recent attacks, researchers from security firm Sophos said, the ransomware has used its access to a targeted machine to install a driver, from Taiwan-based motherboard manufacturer Gigabyte, that has a known vulnerability in it. Despite the vulnerability that led to the driver being deprecated, it retains the cryptographic signature required for it to run in the highly sensitive Windows region known as the Kernel.
Read 7 remaining paragraphs | Comments
Read More